Paid build services are available, contact customer service for details
Secure exchange with the following security defenses:
1: All wallet ports are changed to unconventional ports.
2: Hardware protection (all wallets are put into the intranet machine without any extranet privileges, thus avoiding hackers to call the api interface).
3: Application layer protection, the management background only allows intranet access, isolate the external network on the wallet operation of advanced privileges.
4: Wallet key verification rules using dynamic passwords and static mixed mode to improve the security of the wallet itself.
5: The extranet is accelerated by cdn encryption at sll level to prevent ip leakage.
6: Application wallet access using multisignature in executing a transaction [budget will increase].
7: Add key check to background address and amplify the address length to increase the strength.
8: Change various keys and passwords regularly.
9: For a hundred's of security, it is advisable to transfer large sums of currency to an offline wallet on a regular basis to make it foolproof.
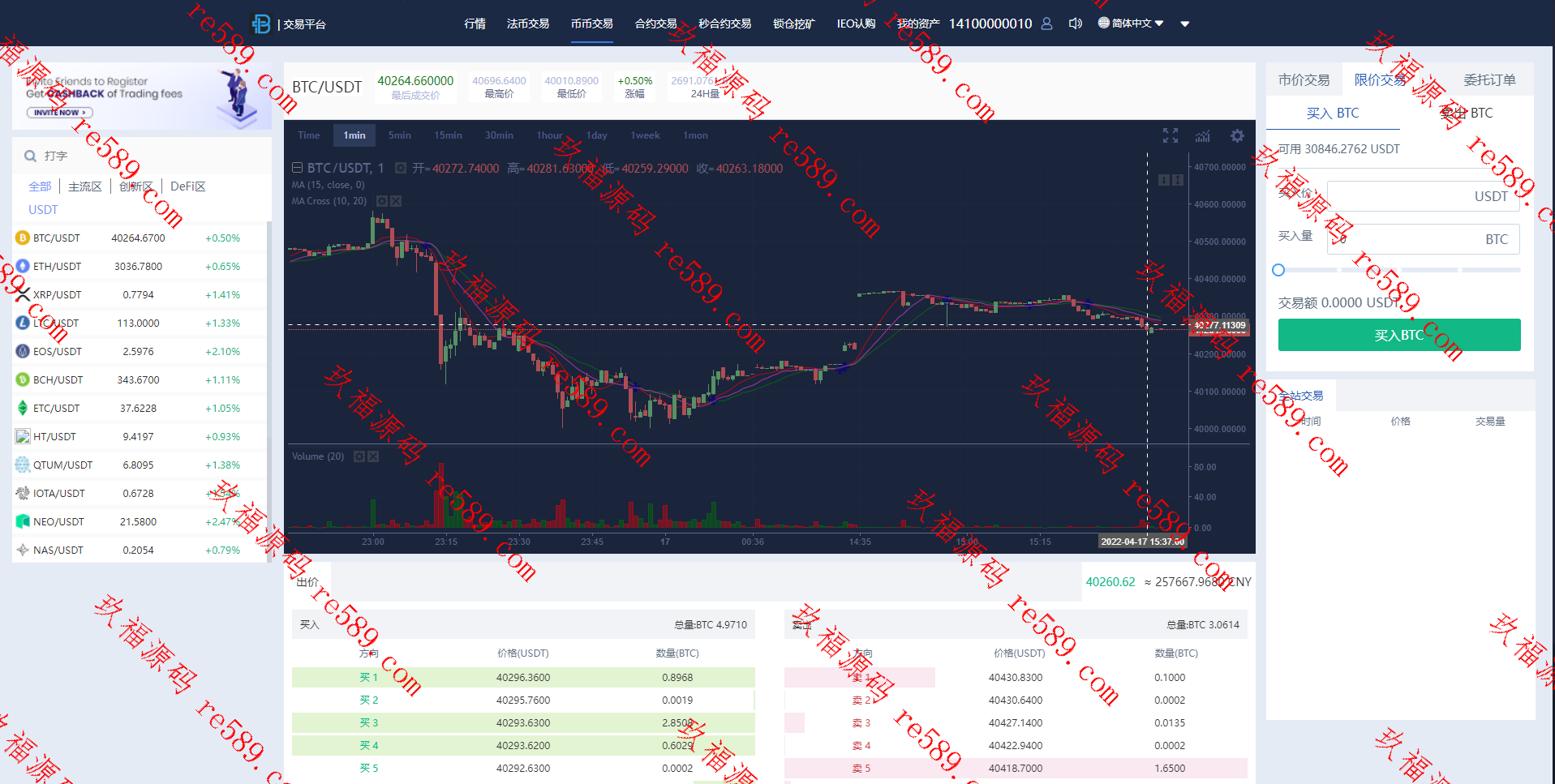
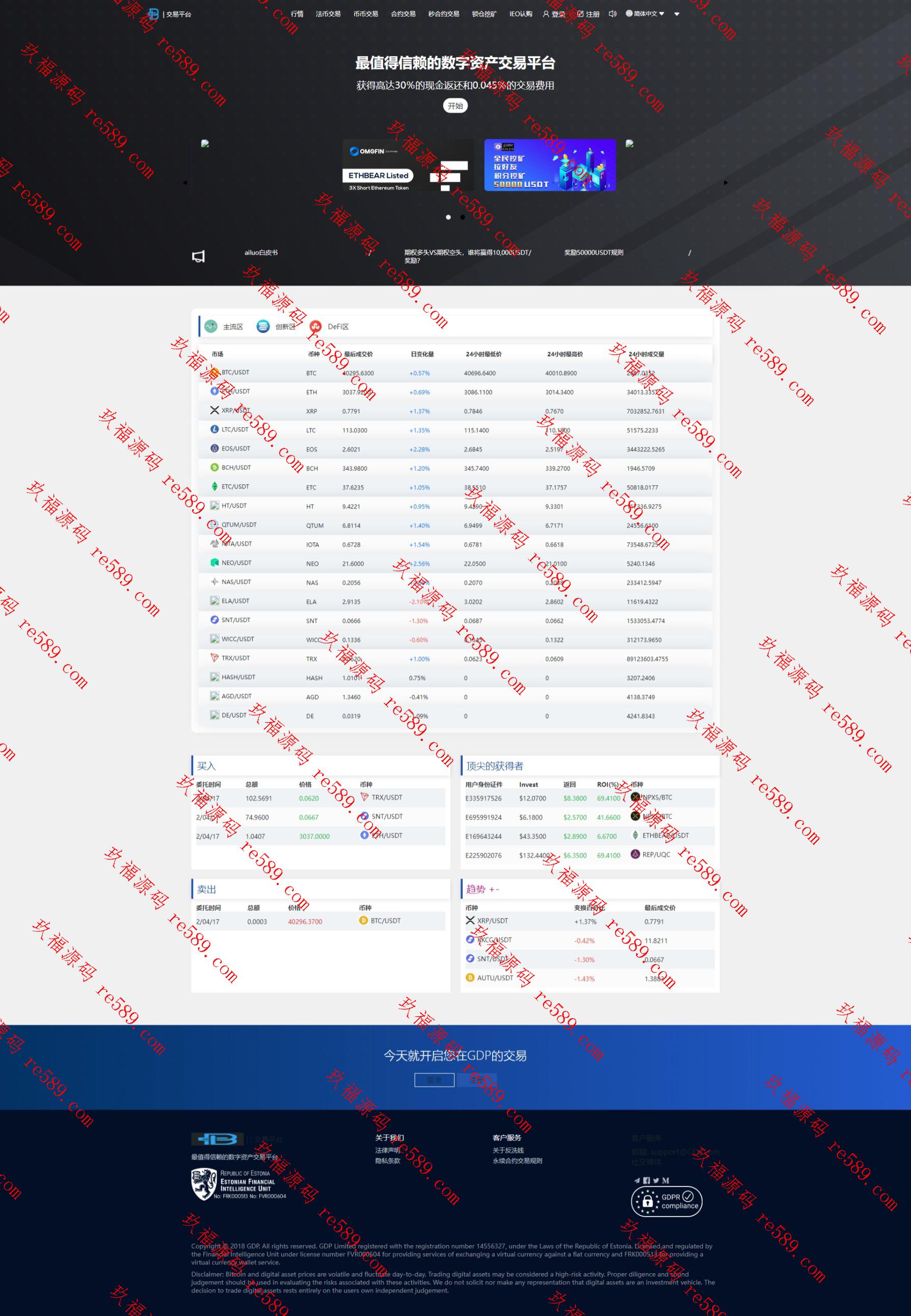
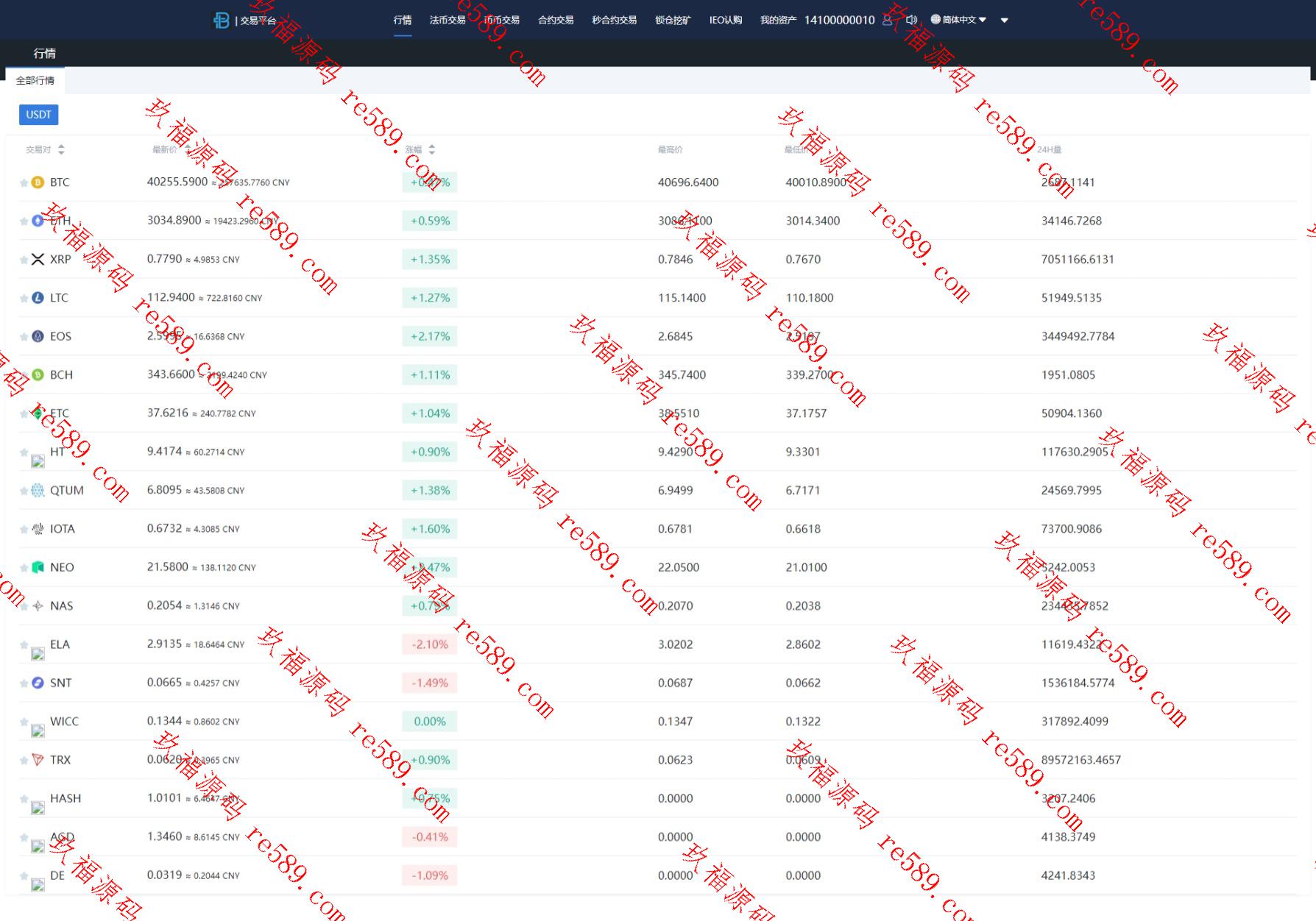
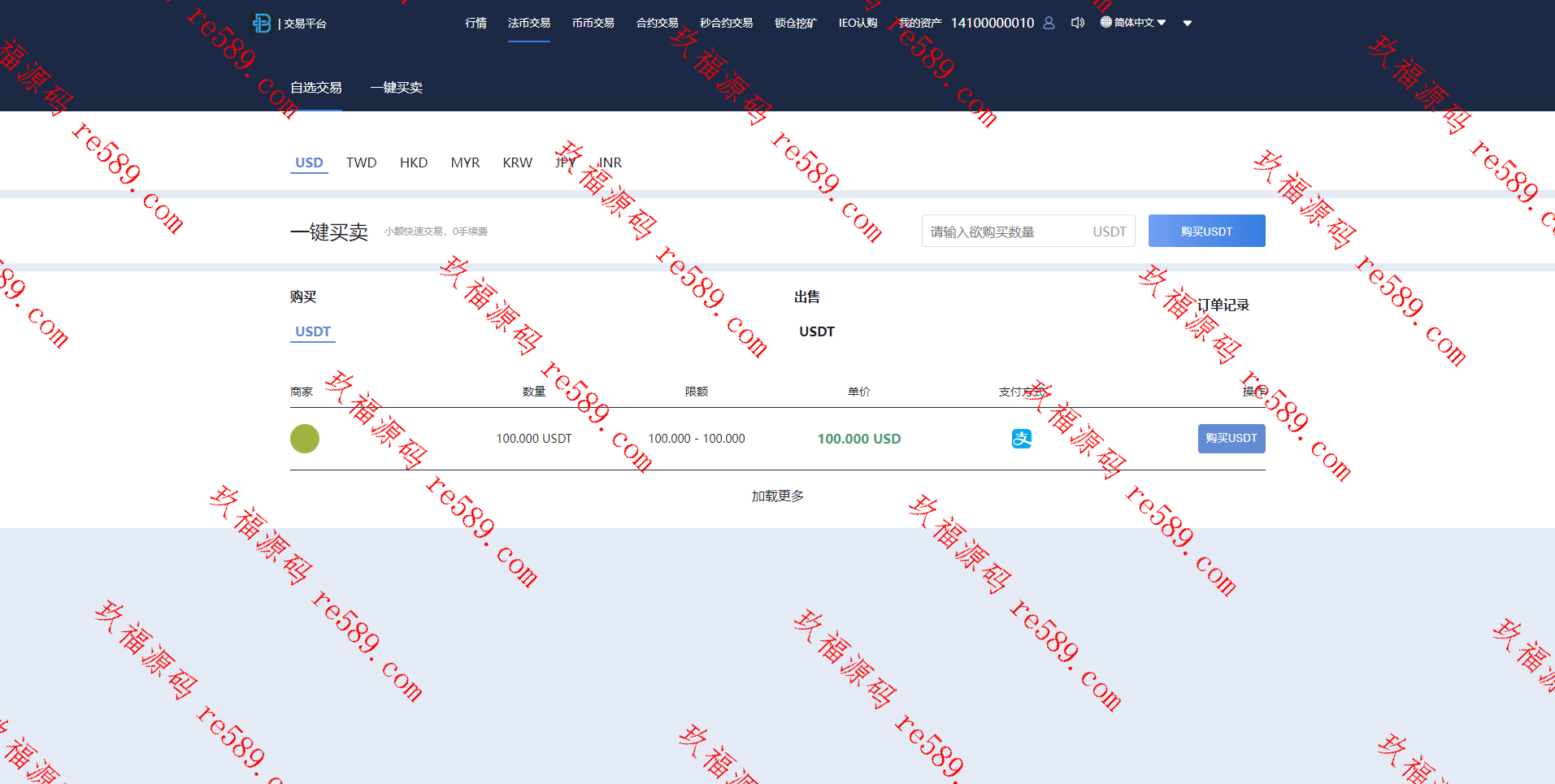
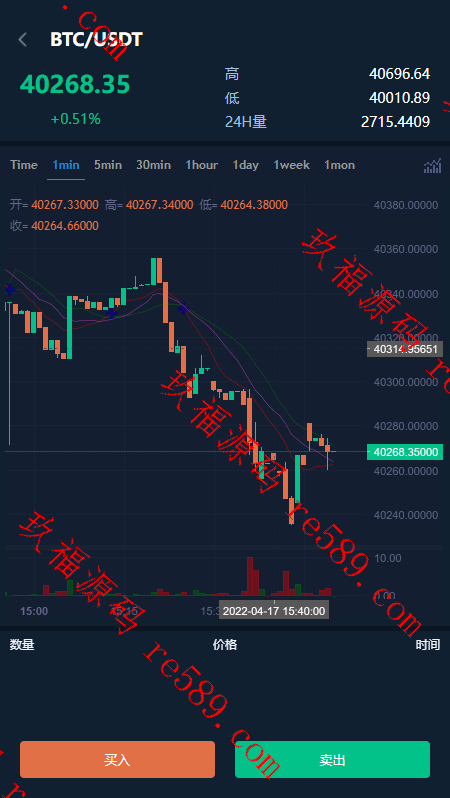
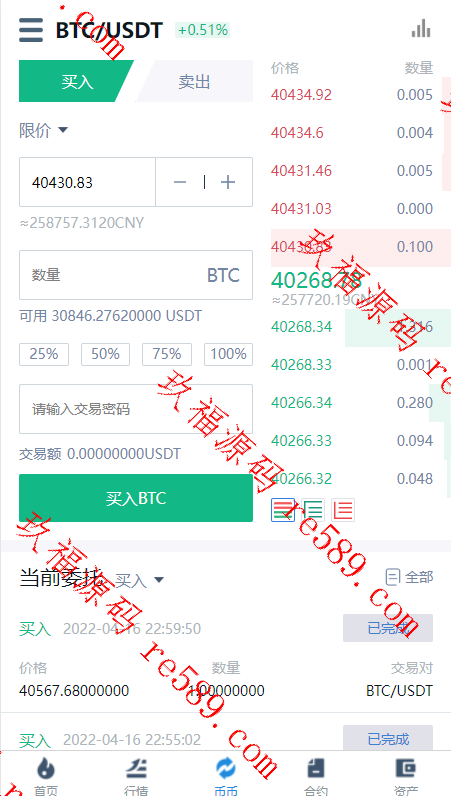
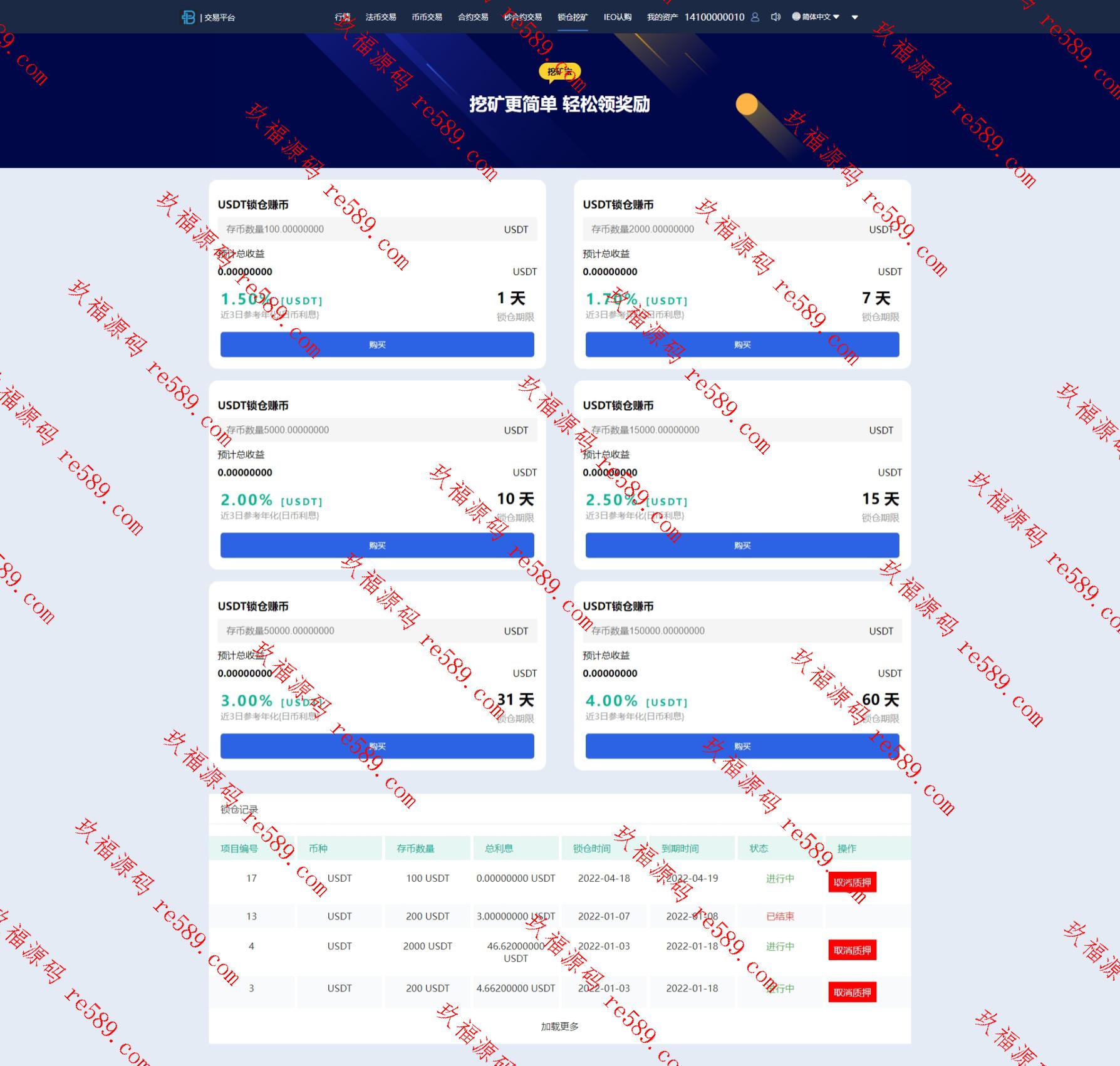
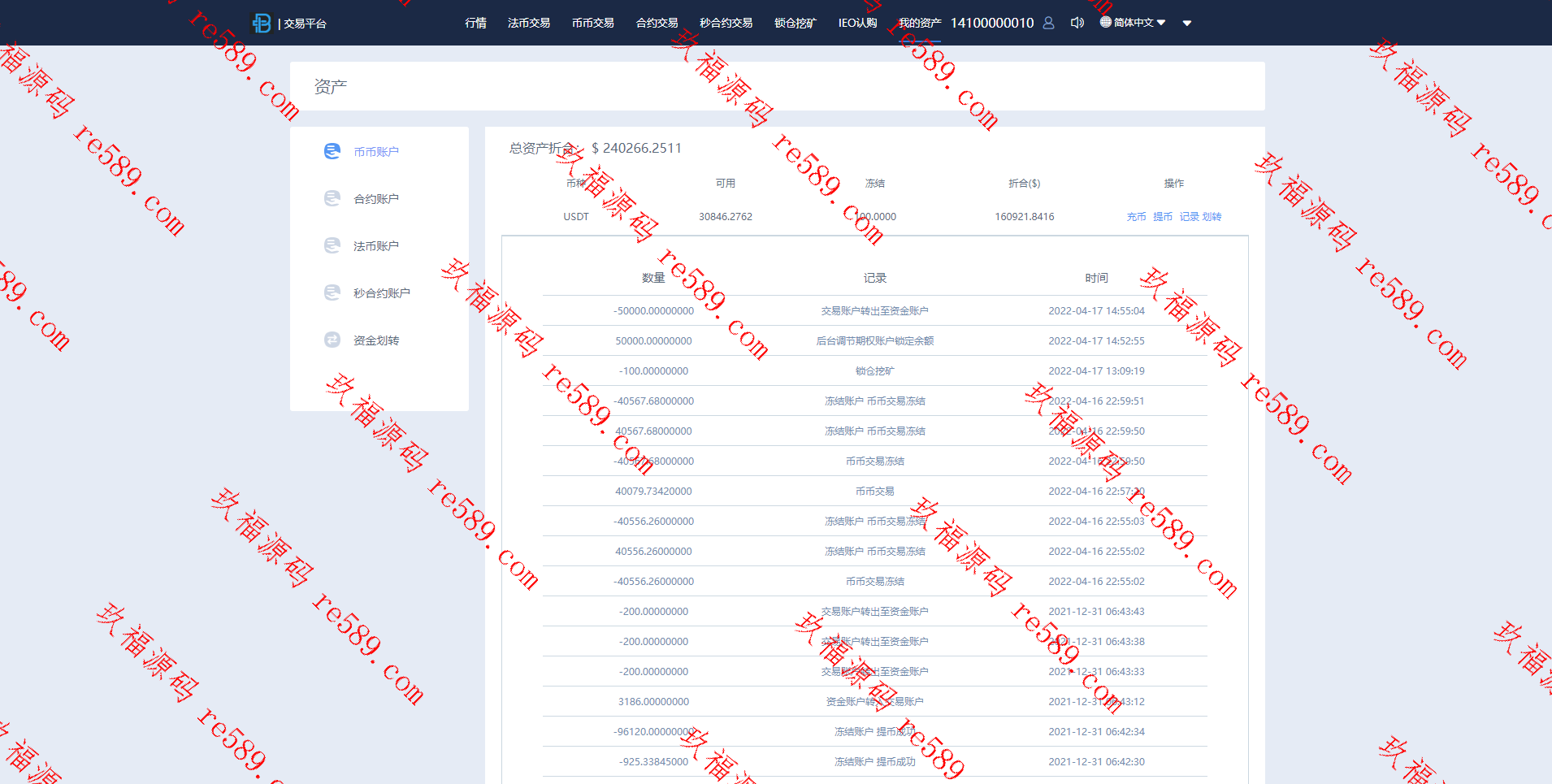
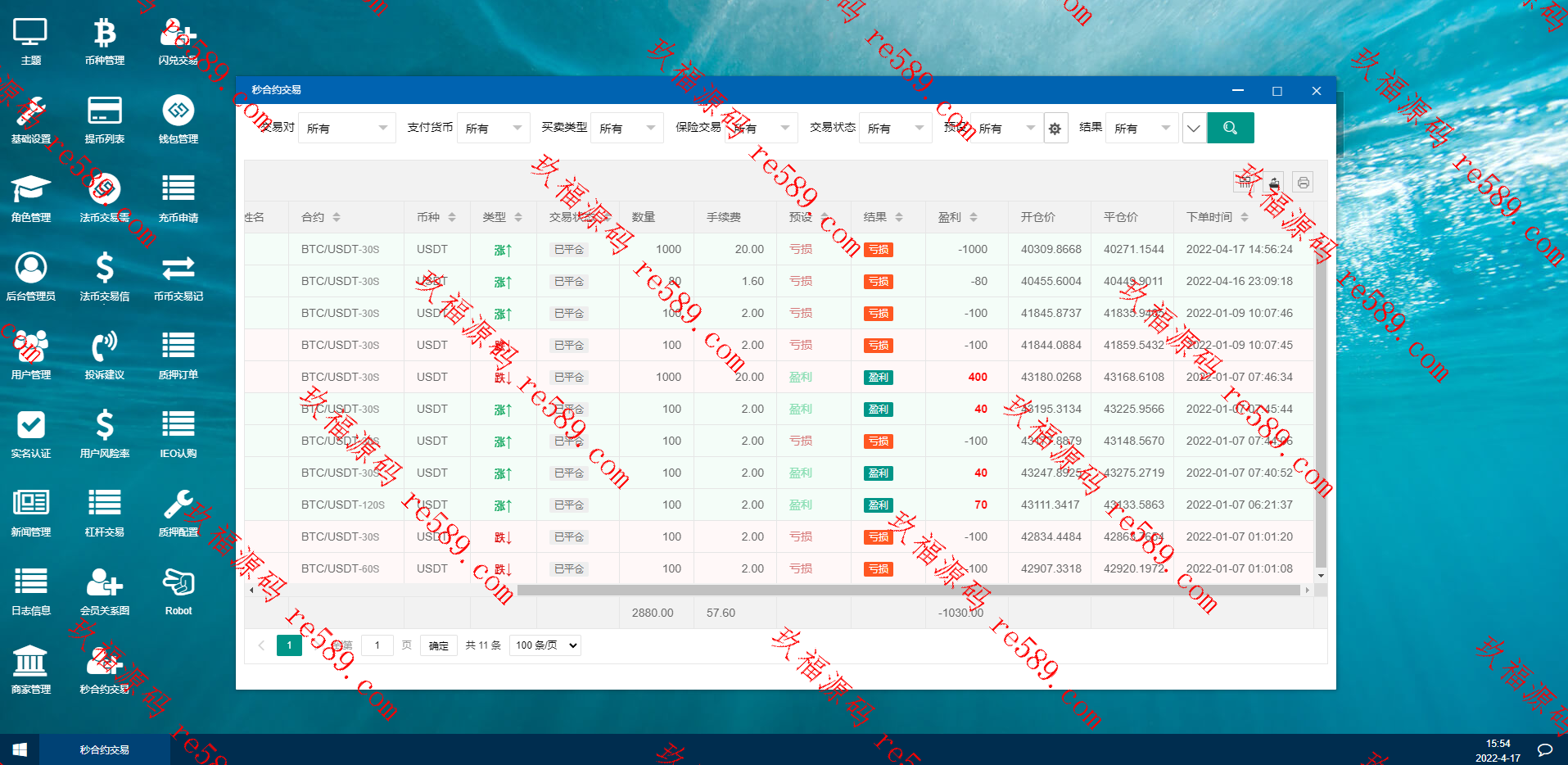
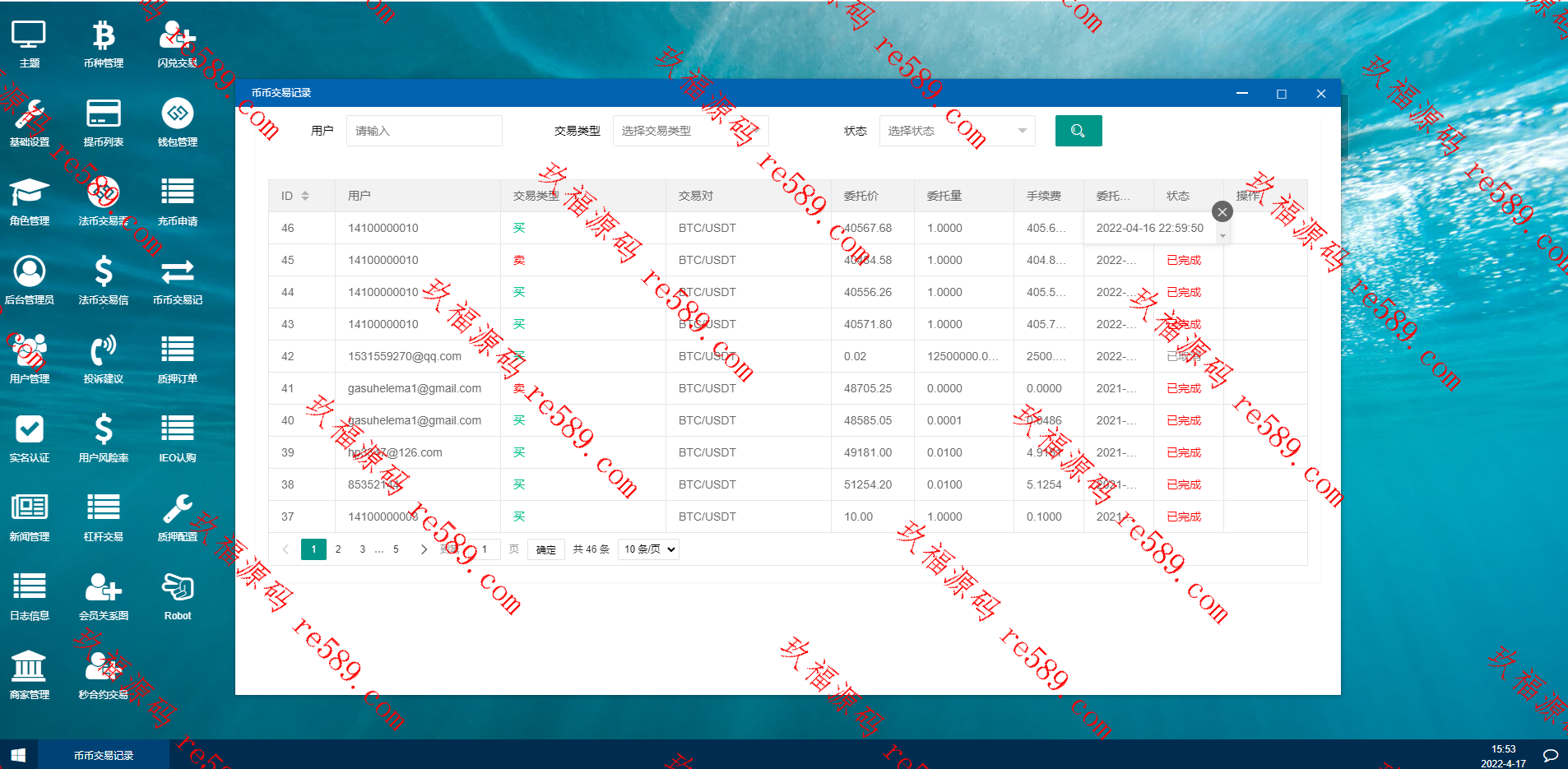
This webmaster can receive secondary development
